|
Search:
Advanced search
|
SSH TunnelingArticle ID: 23
Last updated: 16 Feb, 2015
DetailsIf the customer doesn’t has a static public IP address with the possibility to configure the border router/firewall with port forward or DNAT/SNAT, we could set-up a temporary configuration by using any common Internet connection. Requirements/Conditions/Restraints
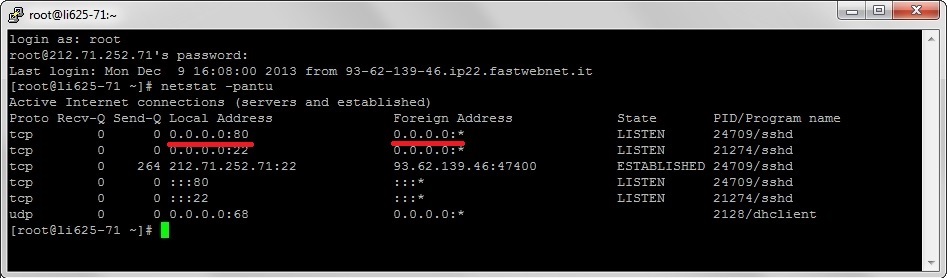
InstructionsA) Configure the server Usually the sshd on CentOS is configured to allow the bridge only on local IP addresses so we need to check the sshd (server) configuration on the Anonymizer/VPS: 1. access the Anonymizer/VPS by using an SSH Client; 2. open with an editor the sshd config file (/etc/ssh/sshd_config), look for the GatewayPorts parameter and check if it’s properly configured to YES without the hash key;
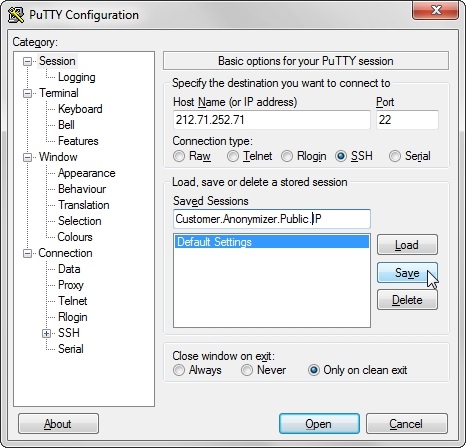
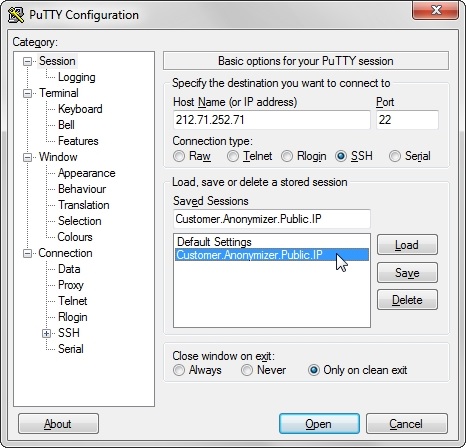
3. save the config file and restart the ssh server. B) Setup SSH Client Configuration Set-Up the ssh tunnel through the SSH Client Configuration: 1. open an SSH Client on the Collector System. This example uses Putty;
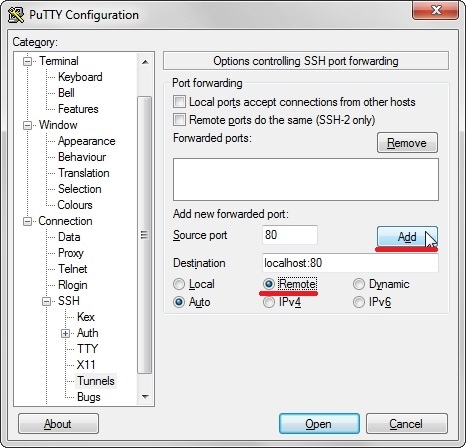
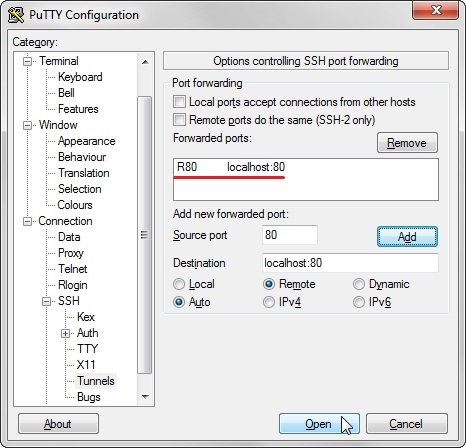
3. explode the SSH config page and move to Tunnels config section;
4. the tunnel will not be ready until you log-in to the Anonymizer/VPS by using a valid pair of credendials;
|
||||||||||||||||||