|
Search:
Advanced search
|
EDN ArchitectureArticle ID: 210
Last updated: 28 May, 2015
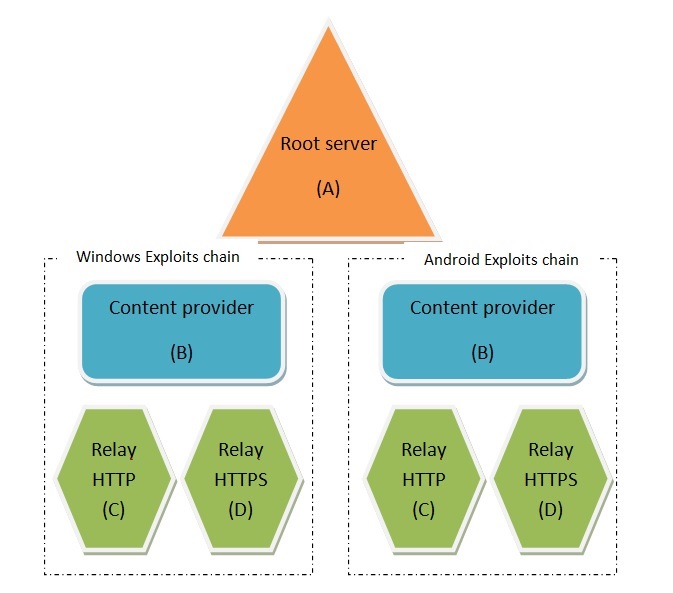
The main componentsThe Exploit Delivery Network service is sold separately; it consists of a root server connected to two chains of servers:
!!! ⇒ Except in some particular cases, all the elements that make up this architecture are controlled directly only by HT, not by customers. On the top of the structure there is the root server (A) used by our Support Team to create the exploits by means of a dedicated console:
!!! ⇒ The data recorded in the content provider do not allow in any way to identify the customer. The collected logs are sent to the root server and are made available by means of the console management interface. The content providers (B) are not exposed to Internet. Each content provider is connected to two relay systems (C, D) and accepts connections only from these machines which serve the exploit:
The communication between the content provider and the relay servers
is authenticated and encrypted (strong encryption is used) in both
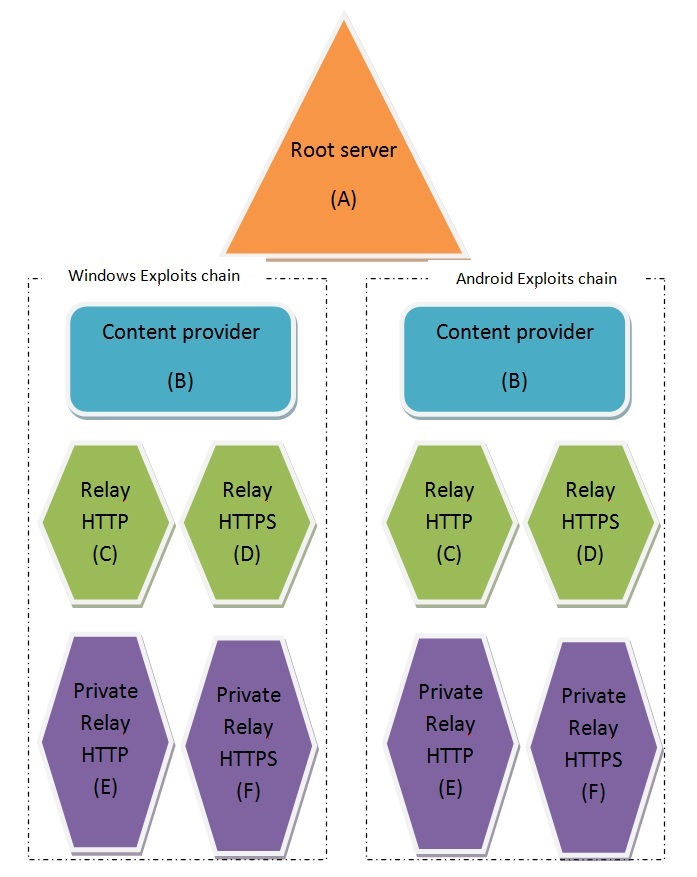
directions. Relay servers under customer controlThe customers who wish to hide the IP addresses of their targets can add to each chain two relay servers under their direct control (E, F).
These relay servers must meet the following requirements:
HT will provide the installation packages compatible with CentOS 6 to be used to install the appropriate services in the customer relay systems. Recommended providersBelow is a list of recommended providers:
Common questionsThe customer wants to know if, in
relation to the download of the exploit from our EDN, something will
remain that can make the target suspicious.
A suspect receives the mail with the exploit and opens it, therefore he will be infected. What happens if (after that) he sends the attachment to an antivirus? What will the antivirus see in the exploits?
Will it be possible to track back the IP address that pushed the download of the backdoor?
Will any trace remain on our EDN?
If the above mentioned
target sends the document to an antivirus without opening it, what
will happen? What will the antivirus see?
|