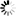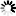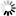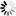|
Search:
Advanced search
|
TNI
How long do the batteries last?
What is the minimum strength of the signal so that there are no problems?
!!! ⇒ As a general rule, before any attack you should run a "Link test" (present on each tab of the Tactical Control Center) and respect the results of the signal levels tests on the sniffing and injection interfaces. Introduction Tactical Network Injector is supplied with pre-installed and set Tactical Device operating system and Tactical Control Center control software. It must be synchronized with RCS server. IMPORTANT: installation requires the Master Node authentication files and synchronization requires the creation of Network Injector on RCS Console. Be well prepared for installations far from the operating center. Package content The package includes a notebook and installation CD. Installation sequence The full installation sequence is provided below: 1 Installing the Tactical Device operating system. NOTE: the operating system is already installed at purchase. 2 Synchronizing Network Injector with RCS server. 3 Checking Network Injector status. !!! ⇒ For more details about installation: TNI installation details.pdf I want to use the URL oracle.com and I would like to have also the URL www.oracle.com. Is it possible to use just one rule with the string oracle.com or I have to create two rules (one with www.oracle.com and another one with oracle.com)?
!!! ⇒ If the resource transmits over HTTPS, you can not do injection. Introduction Tactical Network Injector is a notebook for tactical installation on LAN or WiFi networks. Furthermore, it can be used to unlock the target computer's operating system password to permit physical infections (i.e.: via Silent Installer). Tactical Network Injector uses Network Injector - Tactical Device as an operating system and Tactical Control Center for control software. NOTE: Tactical Network Injector is supplied installed and ready for use, complete with disk encryption and all the foreseen applications. Main functions Tactical Network Injector identifies devices in a WiFi or wired network and injects agents. It works based on identification (automatic or manual) or injection rules set in RCS Console. It can also connect to protected WiFi networks, emulate WiFi network Access Points and unlock the operating system password. Tactical Network Injector communicates with RCS via an Anonymizer (and its chain). Communications are run every 30 seconds to receive identification and infection rules and send status and logs. Its Tactical Control Center control software can be set for remote access. Network connections Tactical Network Injector requires two network connections: one to tap the target's traffic and the other to inject agents and communicate with the RCS server. Tip: after setup, Tactical Network Injector is independent. Internet connection is required to obtain updated rules from RCS and send logs (synchronization). Authentication key An authentication key must be installed on Network Injector to securely communicate with the RCS server. The key must be generated when the Network Injector object is created on RCS Console and installed via Tactical Control Center at the first Network Injector synchronization with RCS. Standard connection layout Typical WiFi layout where Tactical Network Injector is connected to the same WiFi network as target devices.
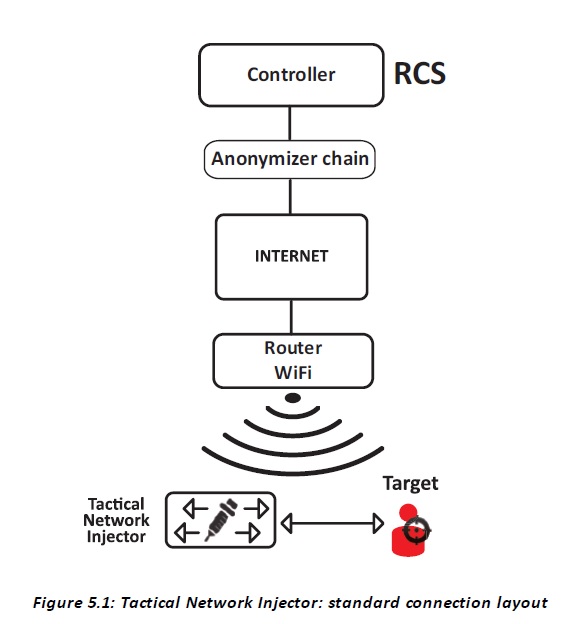
Access point emulation connection diagram Typical layout in WiFi where Tactical Network Injector emulates the open WiFi network access point to attract target devices.
Is it possible to use wildcards in the URL string for INJICT-HTML-FILE rule in TNI device?
If during a WPS attack the laptop runs out of its autonomy, what happens?
!!! ⇒ When you start the WPS attack or any other attack, the system resets the logsystem file, so it is always better to read the file before starting any new attack. |