|
Search:
Advanced search
|
Mobile
What does "Root: yes, Su: no, Admin: no, Persistence: not required[c]" means?
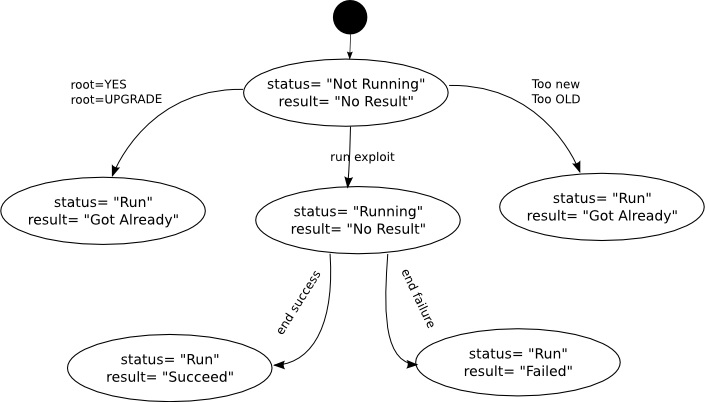
- If required: - Starting state = required, to be installed: - if the root is available, try to install the persistency; the results can be: o failure, installation failed; - If not required: - not required. In the details of the targets I see TIMEOUT. What does it mean?
In the details of the targets I see: UNAVAILABLE. What does it mean?
What can we do if the cp command is not available?
#!/system/bin/sh !!! ⇒ The commands are run as root, both as command and as Upload and execute.
The difference is that the commands cannot be chained in pipes and do
not handle the redirection. Each complex operation should be performed
in a script. If the queues of evidences to be sent from the target to the server are overloaded and create transfer problems:
What
about if I create a new factory and infect the phone one more time
without knowing if the phone was previously infected? Will it work?
Is
it possible to hide or mask/spoof a cell phone number (and perhaps
its IMEI) in order to send a message to a target in such a way that the
SMS appears as it was sent by another number?
If an Android Phone is infected through melted app, should the real app be kept? In case it is uninstalled, is the agent removed too?
After activating the scanning of the file system (in root mode) we realized that many files were missing.
Can I specify the address of the Android remote exploit in the URL of the PUSH Message (Service Load)? Is it advisable to do so?
What is the correct infection procedure and what are the configuration parameters?
!!! ⇒ The configuration dialog has some input fields filled by default; the choice of the input values depends on the type of social attack that the customer is using. The default settings are intended to simulate the sending of an update. In some cases it may be more sensible to simulate the sending of an offer to optimise the tariff of a particular provider. Even the field name must comply with the chosen cover story. I
infected a Blackberry with BASIC configuration via Web link (but also
infecting it with another vector nothing should change) but the phone
will not synchronize, why?
|