|
Search:
Advanced search
|
Desktop
If I have the phone/PC with me, is there a way to know if it is infected (from the device)?
After activating the scanning of the file system we realized that some files were missing. For example, in c:\windows\system32\drivers, the etc folder
was missing as well as a few dozen files on the target machine. We also
tried to Retrieve Subtree directly from the drivers folder with a deep
equal to 3. The missing files did not seem to be neither hidden nor
system files.
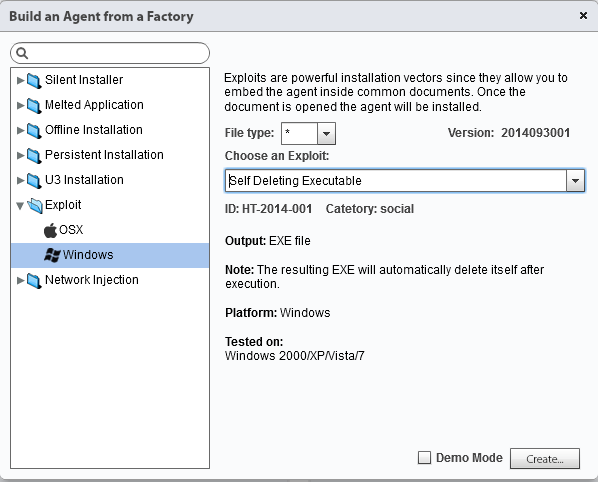
How does the infection "self deleting executable" for Windows PC work?
The system generates an executable file that installs the Scout. After installation, the executable file is automatically deleted without a trace. !!! ⇒ The Scout runs and installs automatically, there is no need to reboot the machine. During
an offline installation from CD, the procedure installed Soldier
instead of Elite. Why did it happen considering that it was an offline
installation?
In a Windows PC that is joined to a domain, does the agent work ?
|